1. Phenomenon
There is a vast range of situations in which you can come across a "domain" on the Internet.
Phishing (password fishing) by email is only one of a large number of cybercrime phenomena.
If you set your email client to display your messages in "original HTML" format rather than "plain text", an offender can "obfuscate" a hyperlink.
The following hyperlink reads microsoft.com, but the site it links to is kernel.org:
A simple and a little bit more evil example with an IDN can you visit here: punny/index.html.
Mouse over the hyperlink and compare it with the address shown in the status bar of your web browser.
A similar situation applies to emails that are shown in "original HTML":

However, if you take a closer look (i.e. view the email source code), you will discover that clicking the hyperlink "https://www.paypal.com/de/verifizieren" would open a different address ("http://83.16.123.18/pp/verify.htm?=https://www.paypal.com/=cmd_login_access") in the web browser:
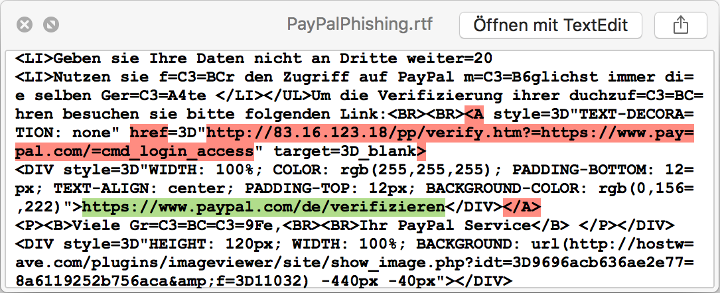
Normally, this address will take you to a form where you are requested to enter login data.
Once the form has been sent, the login data will be transmitted to and stored on the offenders' server.
In most cases, an error message will then appear and you will be taken to the site proper.
There, you can of course log in successfully with our login data.
Websites of banks, savings banks, online payment services (e.g. PayPal), webmail services (to obtain information through a reset, or to send spams) and online shops (e.g. Amazon) seem to be especially worthwhile.
Consequently, further investigations should focus on the URI to which the hyperlink actually leads.